
Cyber attacks can be many things — expensive, embarrassing and dangerous, just to name a few descriptors. And if recent history has taught us anything, it is now crystal clear that major data breaches can happen to anyone from regular Joe's shopping for groceries on their home computers to the world's largest corporations handling terabytes of top-secret information.
There have been many high-profile cyber security incidents over the years but here are some of the worst in terms of their impact...
1. The WannaCry ransomware attack
By the end of this article, you'll realise that 2017 was a bad year for cyber security. In this attack, more than 300,000 computers in 150 countries were attacked in just a few days.
WannaCry was an example of crypto ransomware, a type of malicious software (malware) used by cyber criminals to extort money.
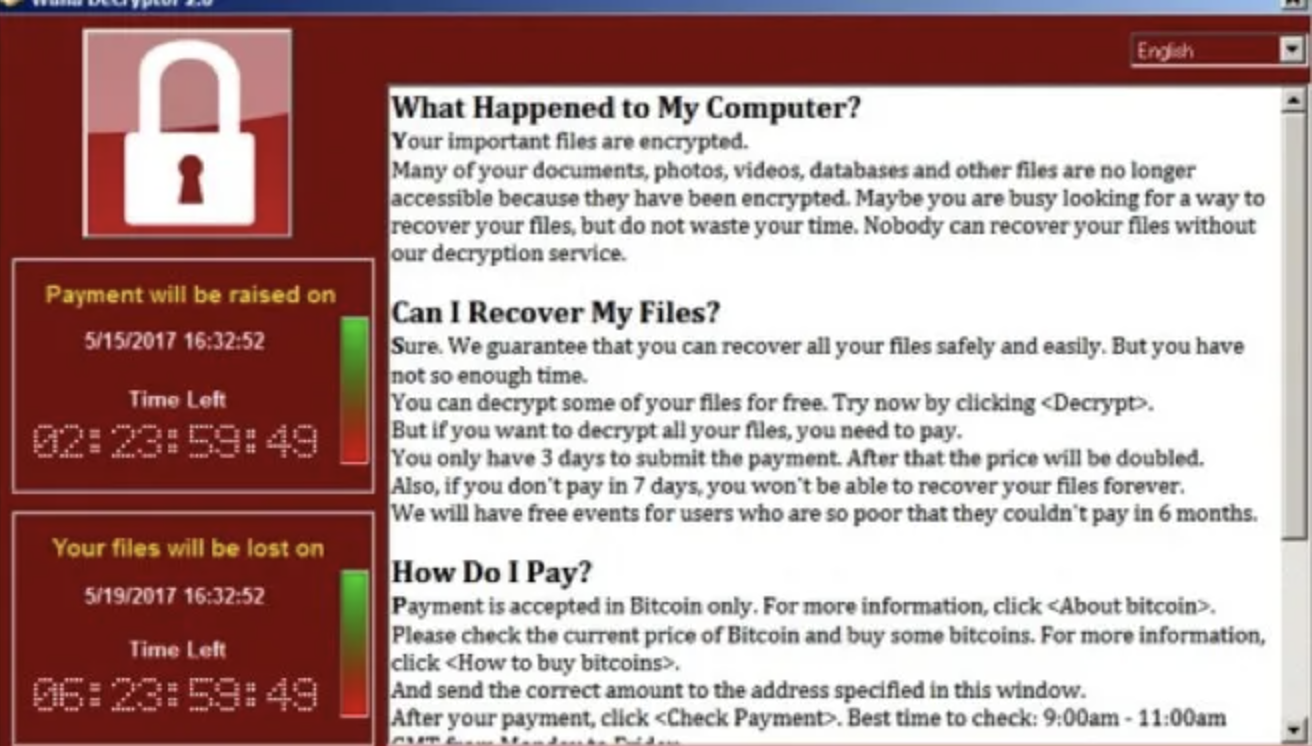
This is what appeared on the computer screens of infected computers. Source: Proofpoint
What makes this attack really horrible is the personal impact it had on so many everyday people. Among the organisations impacted were banks, government agencies and hospitals. Some hospitals had to cancel surgeries and appointments, for example, due to the inability to access patient records. It reported that 20% of the UK's hospitals were impacted by this event.
How did the attack happen?
This global cyberattack targeted computers running the Microsoft Windows operating system by encrypting the data on the infected computer and demanding a ransom payment in exchange for the decryption key.
The WannaCry attack used a vulnerability in Microsoft Windows known as EternalBlue, which was allegedly developed by the US National Security Agency (NSA) and later leaked by a group called Shadow Brokers. The malware exploited this vulnerability to spread rapidly across networks, encrypting data and demanding a ransom payment in Bitcoin.
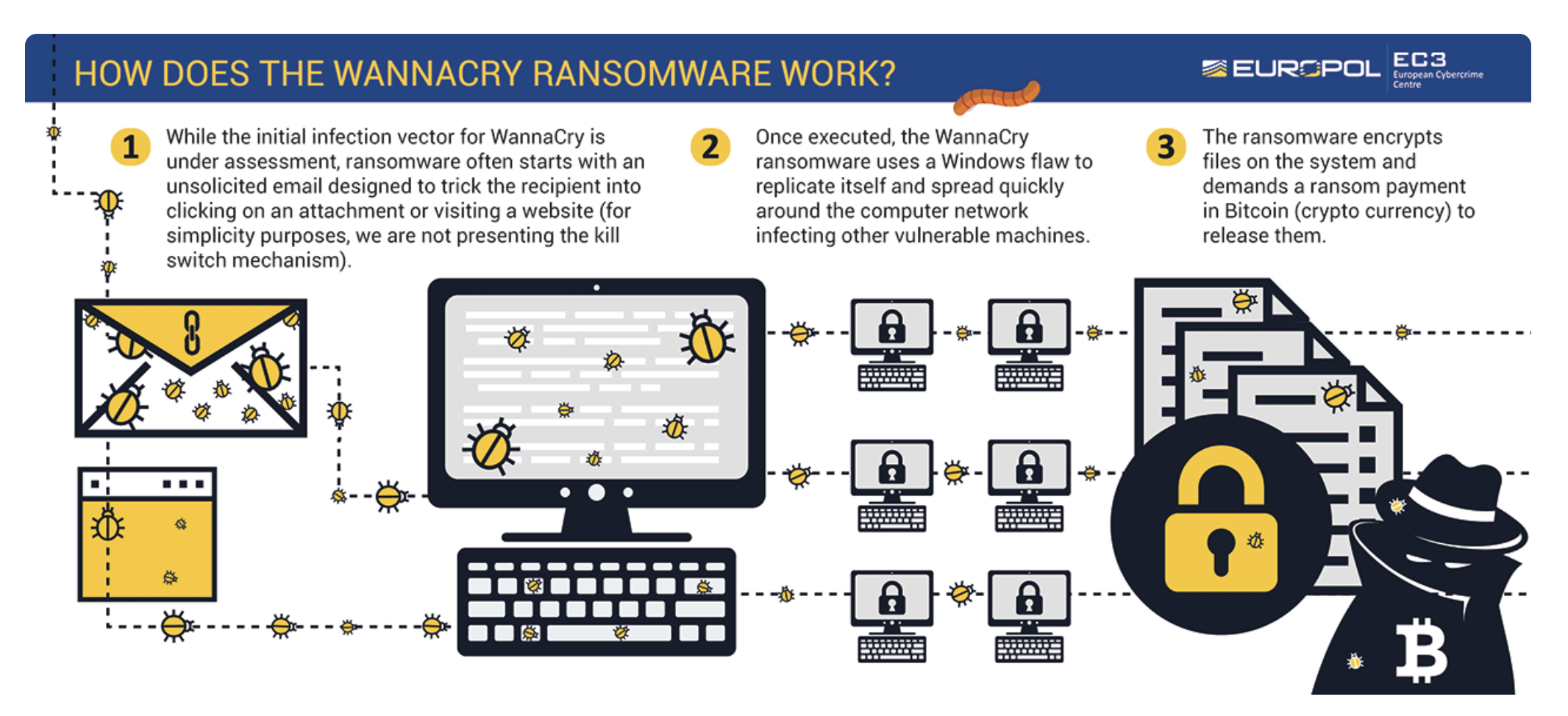
Image source: Europol
Who was responsible for the attack?
As reported in BBC News, both the UK and US governments blamed North Korea for the unprecedented attack. We will likely never know this for sure.
How much did the attack cost?
The attack is estimated to have resulted in financial losses in the billions of dollars.
2. The Sony Picture Hack
In November 2014, skulls appeared on the screens of employees at Sony Pictures, along with a message that ‘secrets’ were soon to be revealed. This was the first sign that the entertainment corporate, a subsidiary of Sony Corporation, had been hacked.
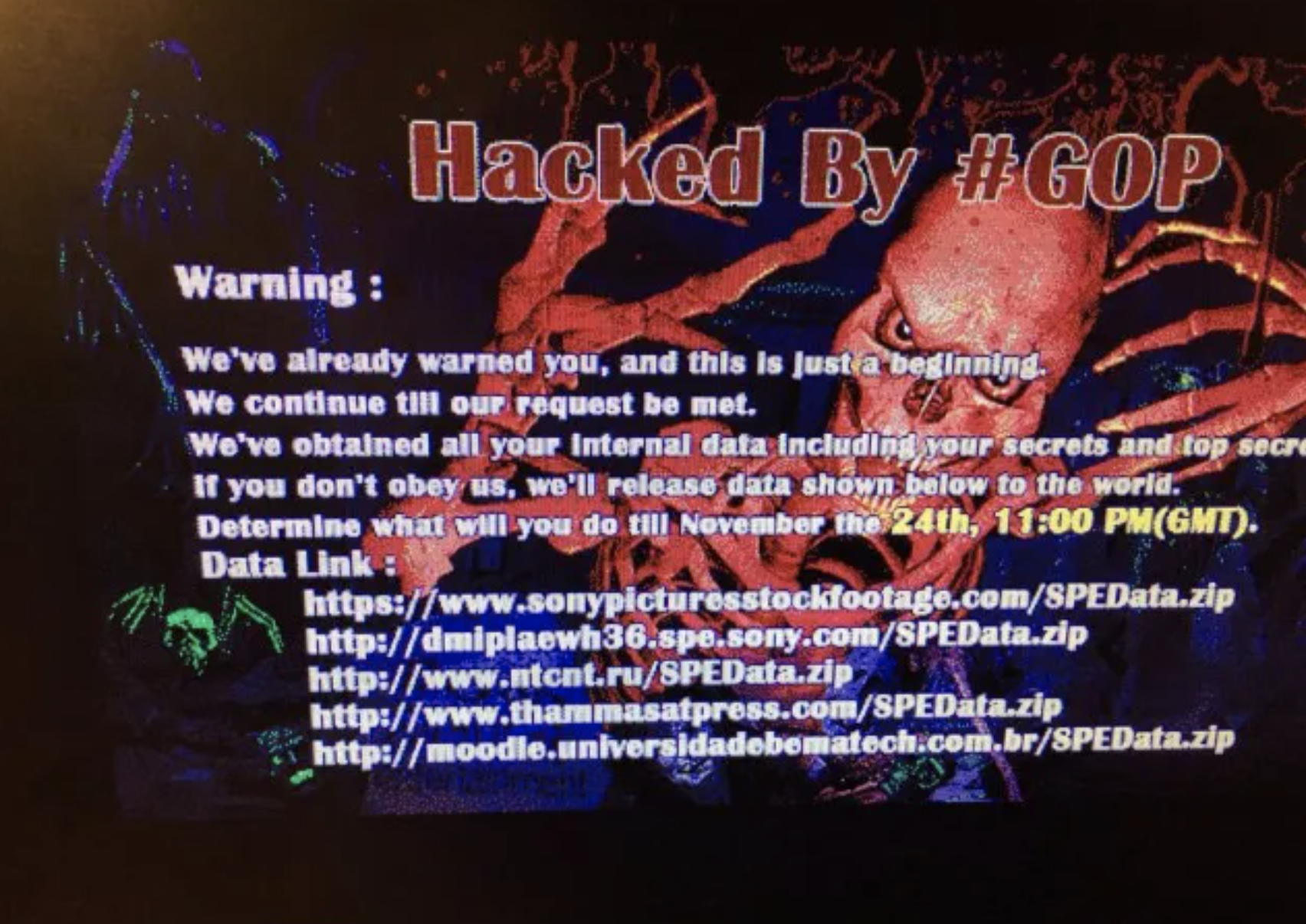 An image posted on Reddit that supposedly shows the screen Sony employees saw when the hack occurred.
An image posted on Reddit that supposedly shows the screen Sony employees saw when the hack occurred.
The hack would go on to reveal loads of embarrassing content for the corp, such as sensitive emails, employee personal information and unreleased movies. Emails that insulted famous actors and actresses; inappropriate internal communications; celebrities’ personal information such as medical and financial records; and data about pay disparities are a few examples of what was leaked.
‘Still Alice’, ‘Annie’ and ‘Mr. Turner’ were among the unreleased films to be leaked online.
The incident even resulted in the FBI issuing a warning to businesses in regards to upping cyber security measures.
How did the attack happen?
While the exact details of the attack are not known, here are some of the key steps that were involved:
- Spear-phishing: The hackers used a spear-phishing campaign to gain access to Sony's corporate network. They sent targeted emails to Sony employees that appeared to be legitimate, but actually contained malware. Once an employee clicked on the link or opened the attachment, the malware was installed on their computer.
- Malware deployment: The malware used by the hackers was a customised version of a piece of malware called Destover. This malware had the ability to spread throughout Sony's network, infecting other computers and stealing sensitive data.
- Data exfiltration: Once the hackers had gained access to Sony's network, they were able to exfiltrate large amounts of sensitive data. They used a variety of techniques to hide their tracks and avoid detection, including deleting logs and using encryption.
- DDoS attacks: In addition to the data theft, the hackers also launched a series of distributed denial of service (DDoS) attacks against Sony's websites. These attacks overwhelmed the servers and caused them to crash, making it difficult for users to access Sony's websites.
Who was responsible for the attack?
While we don’t really know, you will notice a common theme. The US Government has once again attributed the attack to North Korea.
How much did the attack cost?
The exact cost of the attack is unknown. We would estimate hundreds of billions of dollars.
3. The Equifax data breach
In March 2017, the sensitive information of a reported 143 million people entered the public domain - that is more than 40% of the American population. The leaked data included social security numbers, birth dates, addresses, driving license numbers and credit card details. Equifax is one of the credit reporting agencies that assess the financial health of nearly everyone in the United States.
This event was one of the largest data breaches ever in history. Terabytes of data were exposed.
How did the breach happen?
To the best of our knowledge, this is how the breach is thought to have occurred:
- The company was hacked via a consumer complaint web portal. It appears that there was an error in Equifax’s internal processes that allowed this to occur.
- Attackers then moved from this web portal to other servers, as these systems weren’t segmented from one another, and accessed usernames and passwords stored in plain text.
- These usernames and passwords were then utilised by the attackers to pull encrypted data out of the network.
- The attack went undetected for some time as Equifax had failed to renew an encryption certificate on one of their internal security tools.
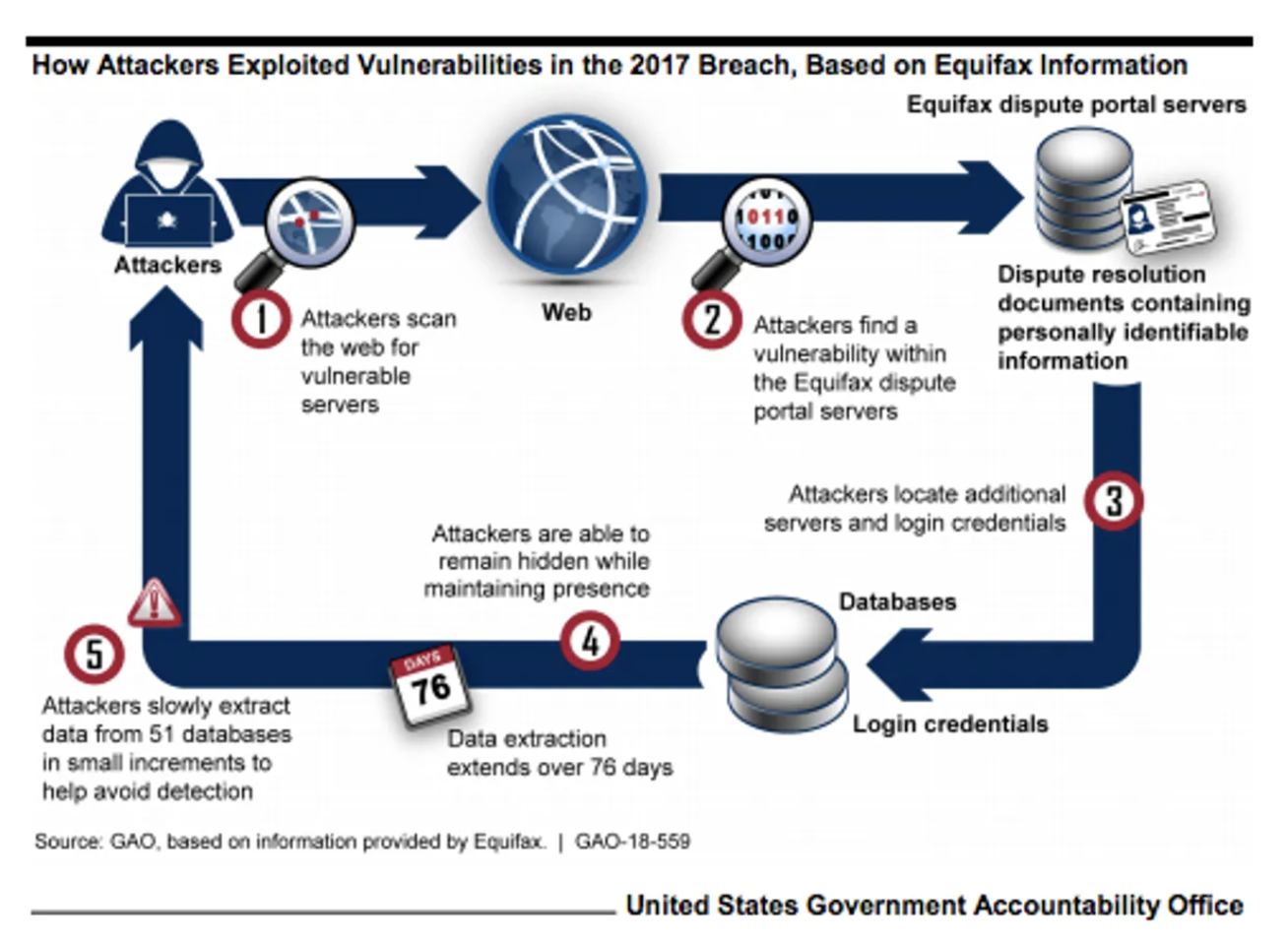
Image source: US Government Accountability Office
Who was responsible for the attack?
While we don’t know who was responsible for the massive 2017 Equifax data breach, a widely believed theory is that Chinese state-sponsored hackers were responsible. This theory stems from the strange fact that the data never appeared on the dark web. Was the motive therefore espionage? We may never know.
How much did the attack cost?
It is reported that Equifax spent a whopping $1.4 billion to improve its cyber security measures in the wake of the attack.
Following a class action suit, at least $1.38 billion was also allocated to resolve consumer claims.
What can we learn from these attacks?
These incidents illustrate the serious consequences that can result from cybersecurity breaches, including financial loss, reputational damage and even threats to national security.
No one is immune. Large corporations, SMEs and individuals are all at risk.
Data breaches are expensive and can be both dangerous and very embarrassing.
No matter the size of your business, It is important to get the basics right. You should enlist the expertise of an IT professional to help you implement and manage the security measures required to protect your data and your business. That is where data governance comes into play.
What is data governance?
While it is increasingly common for businesses both large and small to have cyber security departments which implement technical security safeguards such as firewalls or intrusion detection, there is still a big gap when it comes to the policies, procedures and guidelines that should accompany these practical measures.
When they do exist, policies or processes are often outdated or ignored.
Data governance provides guidelines which help organisations to define how they collect, manage, store, share and use data assets.
In today's modern age, it's an essential part of your everyday cyber security measures - and can help you avoid becoming another cyber attack case study!
How Diamond IT can support your cyber security and data governance measures
Diamond IT's Software Development Team can help you design and build a custom site that will give your team fingertip access to important documentation and streamline processes from a secure, structured platform accessible from virtually any device.
Our Business Technology Managers (BTMs) and Business Technology Consulting team are here to guide you through making the best decisions around technology to support your modern workforce, including how to implement holistic employee experience platforms.
Our team is here to help. Contact us today on 1300 307 907.




