
In this blog, we unveil the significance of this awareness and explore how organisations can better define and manage their data journey, how to classify differing data and when to classify it, increasing the security of your organisations data and the potential risks of data breaches occurring.
Unravelling The Data Journey: Why It Matters
Imagine a puzzle with missing pieces; that's how many organisations perceive their data flow. But comprehending this journey is like gaining a bird's-eye view of your business's nervous system. It's the foundation of robust information security and privacy. By recognising entry points, routes, and exit doors of data, organisations can effectively fortify their defences against potential breaches and unauthorised access.
Mapping the Unseen: Creating An Organisational Data Flow Map
Developing a high-level map of data streams might sound complex, but it's an illuminating process. Picture it as a geographical map, marking sources of information, communication channels, and final destinations. This map is a visual guide, revealing vulnerabilities and opportunities for enhancing data protection.
Microsoft's new tool, Microsoft Purview, enables businesses to catalogue, understand and classify data within the one unified environment. This mapping ability offers organisations the first step in understating their data journey through the following offerings;
- Automate and manage metadata from hybrid sources.
- Classify data using built-in and custom classifiers and Microsoft Information Protection sensitivity labels.
- Label sensitive data consistently across SQL Server, Azure, Microsoft 365, and Power BI platforms.
- Easily integrate all your data catalogues and systems using Apache Atlas APIs.
An example of what a basic map may look like on the Microsoft Purview dashboard sits below.
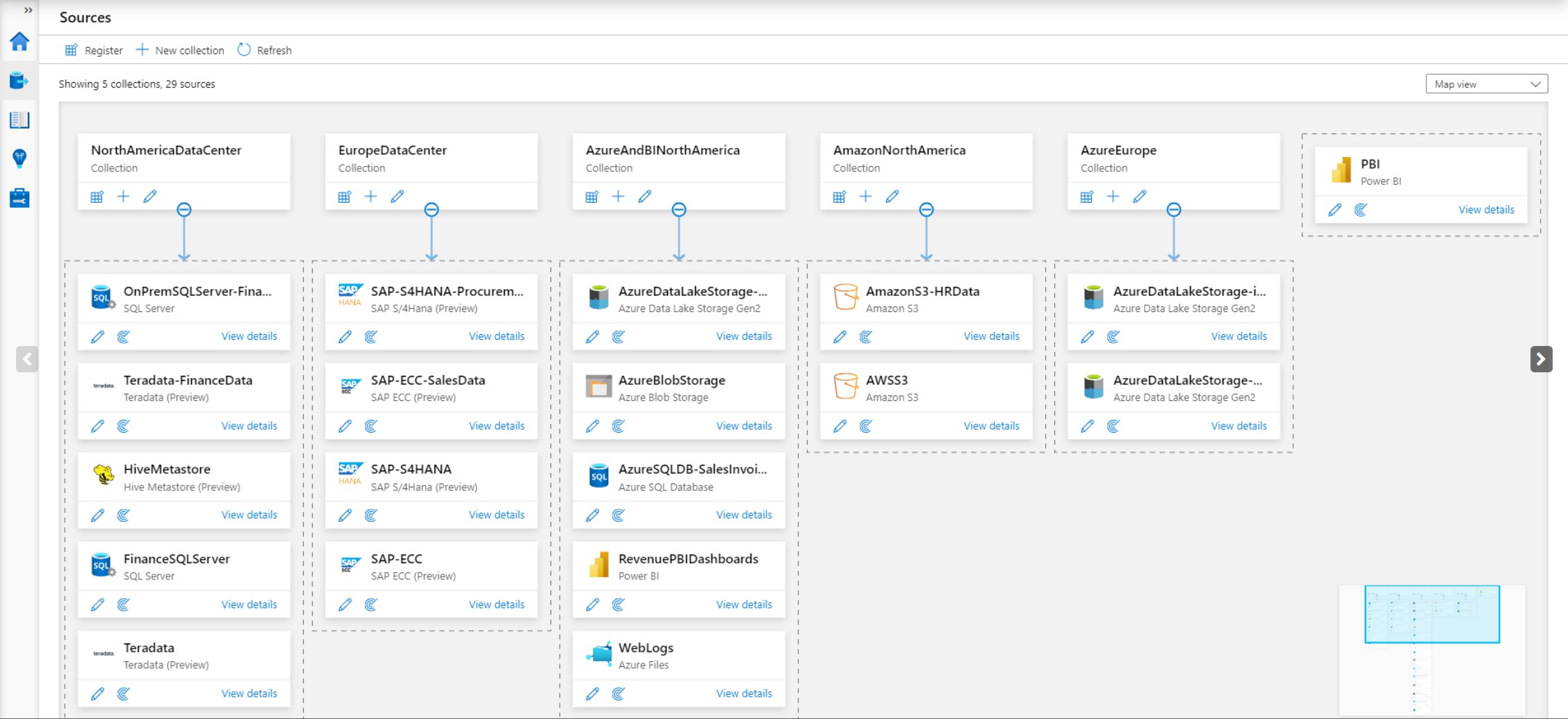
Image Source: Microsoft 'Map Your Data Estate with Azure Preview'
Data Classification: Your Shield Against Chaos
Data classification is the compass that guides teams through the labyrinth of data. It categorises data based on sensitivity and importance. From public information to highly confidential data, each type is treated differently, determining who can access it and how it's handled, ensuring the required security processes are upheld.
Twelve different generic types of data classification are:
-
Confidentiality Classification: This is perhaps the most common type of data classification. It categorises data based on how sensitive it is and who should have access to it. Data might be classified as "Confidential," "Internal Use Only," or "Public," indicating different levels of access control.
-
Criticality Classification: This classification focuses on the criticality of data for the organisation's operations. It helps prioritise data protection efforts. Data can be classified as "Critical," "Important," or "Non-Critical."
-
Personal Identifiable Information (PII) Classification: This classification identifies data that contains personal information that could potentially be used to identify an individual. Examples include names, addresses, social security numbers, and medical records.
-
Data Ownership Classification: This type of classification assigns ownership of data to specific individuals or departments within the organisation. It helps define accountability for data protection.
-
Retention Classification: This classification determines how long data should be retained based on legal, regulatory, or business requirements. Data can be classified as "Short-term," "Medium-term," or "Long-term."
-
Data Sensitivity Classification: Similar to confidentiality classification, this type categorises data based on its sensitivity. It might include levels like "Highly Sensitive," "Sensitive," and "Non-Sensitive."
-
Legal and Compliance Classification: Data that is subject to specific legal or regulatory requirements is classified under this category. It helps ensure that data is handled in accordance with applicable laws and regulations.
-
Access Control Classification: This classification defines who should have access to certain data based on job roles and responsibilities. It helps prevent unauthorised access.
-
Data Lifecycle Classification: Data goes through various stages in its lifecycle, from creation to deletion. This classification considers where data is in its lifecycle and what actions should be taken at each stage.
-
Business Impact Classification: This classification assesses the potential impact on the organisation if the data is compromised. It might include levels like "High Impact," "Medium Impact," and "Low Impact."
-
Third-Party Sharing Classification: Data that is shared with third parties, such as vendors or partners, is classified here. It helps ensure that shared data is protected and used appropriately.
-
Public Disclosure Classification: Data that the organisation is comfortable sharing publicly or with external stakeholders can be classified as such.
The specific classification framework used by an organisation can vary based on its industry, regulatory environment, and unique needs. Proper data classification helps organisations implement appropriate security and privacy measures, allocate resources effectively, and maintain compliance with regulations.
The invisible currents that carry information within organisations hold the key to effective data security and customer trust. By shedding light on these pathways, organisations can not only safeguard their data but also uphold their commitment to privacy and confidentiality.
Through transparent data collection, responsible storage, robust classification, and ongoing training, businesses can navigate the intricate landscape of information security with confidence.
Empowering Your Team: Ongoing Training and Data Governance
Understanding data classification isn't just an IT task; it's a collective effort. Regular training empowers employees to distinguish between data types, grasp their significance, and adopt best practices for data management. This seamlessly transitions into data governance - a framework that ensures data is handled responsibly, ethically, and in compliance with regulations.
How Can Diamond IT Help?
At Diamond IT, our committed team of Business Technology Managers excel in guiding your data security strategies. From Cyber Security Protection and Governance to Endpoint & Application Management offerings, we ensure your data's privacy, confidentiality and all the latest laws and their implications are available to you by Diamond IT - helping you succeed.
Contact us at 1300 307 907 today.




