 By now, every Australian should have a basic level of awareness that their online accounts need to be protected from potential cyber threats. But, did you know that your account could be at risk of a cyberattack, before you even set it up?
By now, every Australian should have a basic level of awareness that their online accounts need to be protected from potential cyber threats. But, did you know that your account could be at risk of a cyberattack, before you even set it up?
Unfortunately, research conducted by Andrew Paverd from the Microsoft Security Response Centre, and independent researcher, Avinash Sudhodanan, has identified a new type of cyber threat which is doing just this, called pre- hijacking.
What is pre-hijacking?
Account pre-hijacking is a new cyber threat in which cybercriminals could gain access to an online account via a new technique that involves laying the foundations for the attack, or 'pre-hijacking' before it's even been registered to the individual.
In pre-hijacking attacks, the attacker predicts which online service will be used by the targeted individual, and conducts certain activities before the user creates their account. When the individual finally joins the site and the account becomes active, the attacker then takes full control.
Which sites are at risk of pre-hijacking?
In the report published by Paverd and Sudhodanan, 75 out of the top 150 websites from the Alexa global website rankings were tested to see if they had pre jacking vulnerabilities.
The attacks are noted to most frequently involve federated identity and single sign-on (SSO) services, which allow users to sign up for certain online services using existing accounts registered with companies such as Microsoft, Google and Facebook.
Of the 150 websites, 136 supported account creation, and out of the 75 tested, 35 appeared exploitable through the pre-hijacking route for at least one attack. Vulnerable sites included:
- Popular social media sites, Instagram and LinkedIn,
- Cloud storage sites such as Dropbox,
- Video conferencing sites such as Zoom, and
- Blogging sites including WordPress.com.
Affected vendors were notified between March and September 2021, but Paverd and Sudhodanan note that many online services could still be vulnerable.
How exactly does pre-hijacking occur?
According to the researchers, "the root cause of account pre-hijacking vulnerabilities is that the service fails to verify that the user actually owns the supplied identifier (e.g. email address or phone number) before allowing use of the account”.
“Although many services require identifier verification, they often do so asynchronously, allowing the user (or attacker) to use certain features of the account before the identifier has been verified. Whilst this might improve usability, it creates a window of vulnerability for pre-hijacking attacks.”
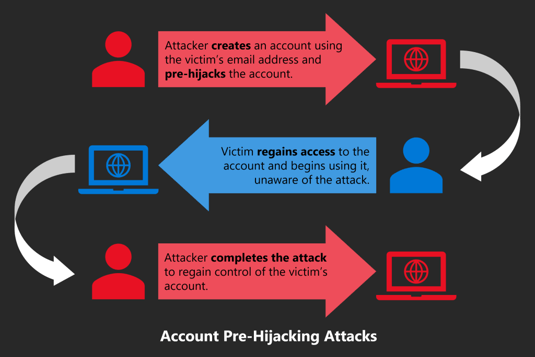
Account Pre-Hijacking Overview
Image credit: Andrew Paverd - Microsoft Security Response Centre
How to protect yourself and your employees from pre-hijacking
Thankfully there are a few simple security provisions you can put in place to make it much more difficult for threat actors who may attempt to orchestrate any kind of credential theft attack. These include:
- Implement and enforce multi-factor authentication on all systems and websites.
- Use a password manager such as LastPass or 1password.
- Keep your browsers up to date.
- Review your account's settings frequently to see if your account has a secondary email address or phone number attached that you do not recognise.
- Educate your employees on known and emerging cyber threats they may encounter, including pre-hijacking.
How Diamond IT can support your cyber security strategy
The Diamond IT team specialise in reviewing cyber security strategies to ensure they are fit-for-purpose, align with government recommendations, and include the necessary defences required to best protect your business from malicious threats.
Our Business Technology Managers (BTMs) and Business Technology Consulting team are specialists in improving your internal cybersecurity and are ready to speak with you. Contact our team on 1300 307 907 today.





