
Have you heard of Living off the Land (LotL)? You'd be forgiven for thinking this may be a type of farming philosophy. However, it actually has nothing to do with growing veggies in the backyard. LotL is a stealthy type of cyber attack posing an increasing risk to businesses globally. It is a technique wherein attackers basically use your own systems against you.
Picture this: Your home is broken into. The robber breaks a window to enter. This is similar to how a traditional cyber attack occurs. Living off the Land techniques are different, sneakier, scarier. To use the same analogy, the robber would observe you, determine where your spare key is hidden, and enter your home using the legitimate method of unlocking the door.
That's what happens when a LotL cyber attack occurs. Metaphorically, anyway.
In more technical terms, LotL refers to a set of strategies and tactics employed by attackers to utilise legitimate tools and resources already present in a targeted system or network for their malicious activities.
Why use this method?
The primary objective of a LotL technique is to minimise the use of malicious code or software that could trigger detection and raise suspicion.
What sort of techniques are used in LotL attacks?
The key aspect of Living off the Land techniques is that attackers utilise legitimate tools and resources, which can make it challenging for traditional security measures to detect their activities.
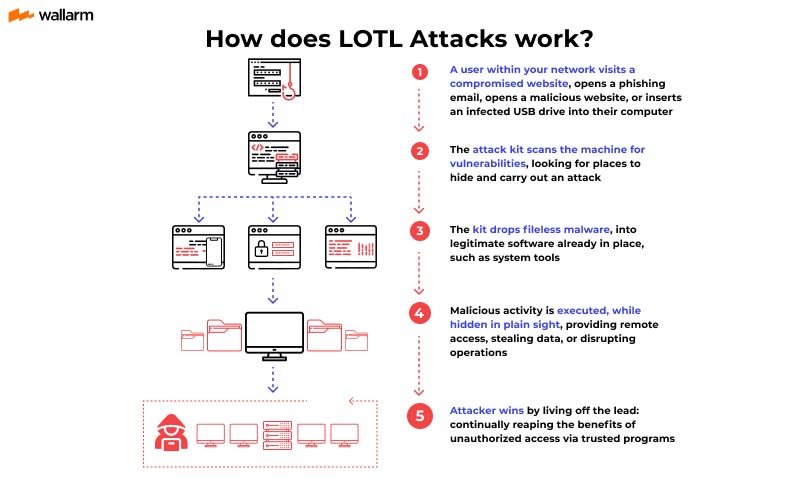
Image source: Wallarm
What are some common methods?
- Fileless Attacks: In fileless attacks, the attacker exploits legitimate system tools or features to execute malicious activities without leaving a traditional footprint. This could involve using scripting languages like PowerShell or Windows Management Instrumentation (WMI) to run malicious code directly in memory, evading detection by traditional antivirus software.
- Credential Theft and Abuse: Attackers may employ various methods to steal credentials, such as keyloggers, password-cracking tools or social engineering techniques. Once they have gained legitimate credentials, they can abuse them to move laterally within a network or escalate privileges, effectively "living off the land" by using authorised accounts.
- System Tools and Utilities: Attackers may leverage existing system tools and utilities already available on targeted systems, such as command-line interfaces (e.g., Command Prompt, PowerShell), network administration tools (e.g., Netsh, PsExec), or scripting languages (e.g., VBScript, JavaScript) to execute malicious commands or scripts.
- Trusted Applications: Instead of introducing new malicious software, attackers may compromise or exploit trusted applications that are commonly used within a target environment. They can abuse the functionality or vulnerabilities of these applications to carry out their malicious activities, making it difficult to detect their presence.
- PowerShell Abuse: PowerShell, a powerful scripting language available on Windows systems, is often targeted by attackers. They can use PowerShell to execute malicious commands, download additional malware, or conduct reconnaissance within a compromised network.
- WMI Abuse: Windows Management Instrumentation (WMI) is a management technology present in Windows operating systems. Attackers can abuse WMI to execute commands, perform system reconnaissance, or transfer files within a compromised network.
Living off the Land in action: The NotPetya Ransomware Attack (2017)
A summary of the attack:
- The attack was primarily Ukraine-based but impacted companies globally.
- It caused financial loss, operational disruption, and damage to critical infrastructure. Read our blog about what the Australian Government has done to protect businesses dealing in critical infrastructure.
- Companies such as Maersk, FedEx, Merck, and numerous Ukrainian government agencies were among the victims, experiencing widespread system outages and disruptions to their operations.
Image Source: crowdstrike
The massive cyber attack known as NotPetya wreaked havoc worldwide, targeting companies primarily in Ukraine but also around the globe.
NotPetya was a destructive ransomware attack that employed Living off the Land techniques to propagate and cause extensive damage.
It all kicked off when a Ukrainian accounting software company, M.E.Doc, was compromised. Attackers infiltrated M.E.Doc's systems and planted malicious code within a software update. As M.E.Doc's software was widely used by various organisations for tax reporting purposes, the attackers exploited the trust associated with the legitimate software and distribution channels.
When organisations downloaded and installed the compromised software update, the malicious code embedded in it triggered the NotPetya ransomware. NotPetya was designed to spread rapidly within networks by exploiting multiple vulnerabilities, primarily through administrative tools and Windows Management Instrumentation (WMI).
Once inside a network, NotPetya employed Living off the Land techniques to move laterally and escalate privileges. It used legitimate tools like PsExec and Windows Management Instrumentation Command-line (WMIC) to execute malicious commands and gain control over other systems within the network.
The attackers also exploited a known vulnerability in the Microsoft Windows Server Message Block (SMB) protocol called EternalBlue, which was previously utilized in the WannaCry ransomware attack. EternalBlue allowed NotPetya to propagate across the network without user interaction.
NotPetya's primary objective was to cause widespread disruption and destruction. The ransomware encrypted critical files and master boot records, rendering infected systems inoperable. It also modified the Windows' Master Boot Record (MBR) to make the infected machines unbootable.
The attack had a significant impact on organisations worldwide, causing financial losses, operational disruptions, and damage to critical infrastructure. Companies such as Maersk, FedEx, Merck, and numerous Ukrainian government agencies were among the victims, experiencing widespread system outages and disruptions to their operations.
How do I protect my company against LotL cyber attacks?
Defending against LotL attacks typically requires a multi-layered security approach, including monitoring and analysis of system logs, network traffic, user behaviour and the deployment of advanced threat detection solutions that can identify anomalous or suspicious activities.
Here are some key steps companies can take:
- Cyber Security Awareness Training.
- Restricted Access and Administrative Privileges: Implement the principle of least privilege, ensuring that users and systems have only the necessary permissions and access rights required to perform their tasks.
- Patch Management.
- Application Control / Whitelisting: Allowing only approved and trusted applications to run within the network environment.
- Network Segmentation: Divide the network into smaller segments or subnets to restrict lateral movement for attackers.
- Endpoint Protection.
- Monitoring and Log Analysis.
- Privileged Access Management (PAM).
- Security Information and Event Management (SIEM) with an added Security Operations Centre (SOC).
- Regular Security Assessments.
- Incident Response and Recovery.
- Security Updates and Threat Intelligence.
Remember that no security measure is foolproof, so it is crucial to adopt a layered defence approach that combines multiple security controls, regular monitoring, and employee vigilance to mitigate the risks associated with LotL cyber attacks.
How Diamond IT can support your cyber security strategy
Do you need help protecting your business from the ever-increasing and evolving threat of cyber attack? The Diamond IT team specialises in reviewing cyber security strategies to ensure they are fit-for-purpose, align with government recommendations and include the necessary defences required to best protect your business from malicious threats.
We can support you by establishing your Essential Eight maturity level and improving your overall cyber security posture through our range of Managed IT Services options which are aligned to the Essential Eight mitigation strategies.
Our endpoint and application management offering is designed to help you protect your devices and applications from cyber attacks, including application patching which ensures that all of your applications are consistently patched to reduce the risk of vulnerabilities.
Our services also include controlling application installation and execution to prevent malware and unauthorised software, securing Office Macros to authorised users only, and restricting access to functions vulnerable to cyber-attacks through application and endpoint hardening.
Finally, our mobile device management (MDM) service allows you to control applications, settings, and track devices, giving you the ability to reset them in the case of theft.
Our Business Technology Managers (BTMs) and Business Technology Consulting team are specialists in improving your internal cybersecurity and are ready to speak with you. Contact our team on 1300 307 907 today.





