
Your devices are your gateways to the digital world. Secure them, and you secure your organisations future.
In an increasingly digital world where smartphones and tablets have become integral to our personal and professional lives, managing these devices securely has become paramount. Re-enter Mobile Device Management (MDM), a crucial technology that can ensure the safe and efficient operation of mobile devices within organisations.
In this blog, we'll break down what MDM is, why it's a hot topic right now, potential risks and how to mitigate them, the regulatory landscape, and why it's indispensable for businesses.
Simplifying MDM: Your Digital Guardian
Imagine MDM as a digital guardian for your mobile devices. It's a comprehensive solution that allows organisations to manage and protect devices, including smartphones and tablets, across their network. With MDM, administrators can remotely control and configure devices, enforce security policies, and even remotely wipe data if a device is lost or stolen. This technology provides a seamless way to manage device settings, applications, and security measures from a centralised platform, ensuring a consistent and secure user experience.
Why Is MDM Still Making Waves Today?
The world of work has undergone a seismic shift, embracing remote operations and the 'Bring Your Own Device' (BYOD) trend. This shift has thrust MDM back into the limelight, now increasing types of device management to 4;
- Bring Your Own Device - (BYOD)
- Choose Your Own Device - (CYOD)
- Corporate/Company Owned Personally Enabled - (COPE) &
- Corporate/Company Owned, Business Only - (COBO)
The areas of user experience, device fragmentation, systems integration and data security are just some of the challenges that these increasing types of device styles raise.
Imagine this scenario: a company employee inadvertently leaves their laptop containing critical customer information on a train during their commute. Suddenly, sensitive data is at the mercy of unknown hands. The repercussions could range from financial loss to reputational damage. This risk is further exacerbated when employees store important data on their personal devices, blurring the lines between personal and professional use.
Implementing stringent security protocols such as full-disk encryption and biometric authentication can act as a first line of defence. Regular training sessions that emphasise the importance of data security and the proper handling of devices can also create a culture of vigilance within the organisation. Additionally, adopting remote data wipe capabilities can provide a fail-safe mechanism to erase sensitive information from lost or stolen devices which is included in a basic MDM offering.
Microsoft, a tech titan, recognises this seismic shift and has been actively shaping the landscape, with software like Microsoft Intune. As more employees use BYOD and COPE device styles the need to secure sensitive information and maintain data integrity has skyrocketed. Microsoft MDM solutions through their Intune offering has been at the forefront of this changing landscape, addressing these concerns head-on and providing strategies to help secure organisations data while allowing access for efficient productivity to be achieved.
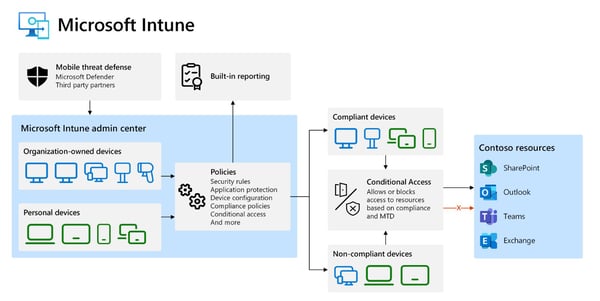
Image Source: Microsoft Intune
In today's digital landscape, where smartphones are constantly at our fingertips, MDM emerges as a crucial time-saving tool with substantial ROI potential, particularly for small and medium-sized businesses. MDM empowers organisations to exert frameworks over app downloads, allowing them to curtail the installation of games and external messaging apps on company platforms. While this level of control is more difficult in the duel use devices, organisations can enforce clear update and patch management protocols that encompass any device accessing the network through automation and regular device update status audits. This will ensure devices receive critical security updates in a timely manner, regardless of their location or ownership and can provide insights into potential security gaps that need immediate attention.
By treating all devices as potential points of entry for cyber threats, organisations can create a more robust and secure digital ecosystem.💼📱💡
Regulatory Landscape & Insurers' Demands
In the dynamic landscape of mobile technology, the regulatory environment of 2023 has undergone a significant transformation, impacting businesses, particularly small and medium-sized enterprises. Regulatory bodies are now placing heightened emphasis on mobile device management practices, demanding rigorous adherence to safeguard sensitive data and protect user privacy. Simultaneously, insurers are setting stringent criteria for cyber security measures, making MDM a non-negotiable aspect of risk management.
For organisations, this means that implementing robust MDM strategies is no longer an option but a necessity to navigate the intricacies of compliance and to satisfy insurers' requirements. As the digital realm continues to evolve, staying ahead of these regulatory and insurance-driven changes ensures not only business continuity but also a fortified defence against cyber threats in an ever-connected world. This is illuminated in articles like that published by Brynn Abbot (a UK MDM & IT Specialist), which delves into the cyber insurance landscape and its connection to the importance of having mobile device management.
Why MDM Is Essential
While MDM has been seen as a bedrock item for SMB cyber security for some time, it is now seen as a necessity. It not only protects sensitive data but also empowers businesses to navigate the complex landscape of modern technology securely. As the digital realm continues to evolve, MDM stands as one of the many indispensable shields, fortifying organisations against threats and enabling them to thrive in the digital age.
The ubiquity of digital devices has made them an integral part of both personal and professional landscapes. However, this increased usage has also made devices prime targets for cybercriminals seeking to exploit vulnerabilities for malicious purposes.
Hackers constantly probe for weak points in devices' security defences. These vulnerabilities can range from unpatched software to inadequate firewall protection. Once exploited, cyber criminals can gain unauthorised access to an organisation's network, leading to data breaches, malware infections, and other devastating consequences.
Mitigating Risks With MDM
To mitigate this risk, organisations must adopt a proactive approach with regular security audits, penetration testing, and vulnerability assessments to help identify potential weak points before they are exploited. Implementing robust antivirus and anti-malware solutions can provide an additional layer of defence against external threats. Moreover, fostering a culture of cyber security awareness among employees like that of the training sessions suggested above will aid employees in recognising and correctly reporting suspicious activity promptly.
By embracing MDM, organisations exhibit their commitment to data security, regulatory compliance, and maintaining customer trust.
Explore the small business checklist from the Australian Government's Australian Cyber Security Centre (ACSC) to ensure your business is effectively safeguarded. Take the vital steps to enhance your business's security posture by referring to this valuable resource today.
How Can Diamond IT Help?
At Diamond IT, our team of Business Technology Consultants is dedicated to helping you choose the right security solutions for your business needs. Through our comprehensive Managed Service Agreements (MSA), we ensure thorough cyber defence and data protection. This is particularly important for individuals using mobile devices, ensuring secure and optimised operations.
Aligning Managed IT Services with the Essential Eight strategies
We enhance your cyber security stance by assessing your Essential Eight maturity level and offering Managed IT Services aligned with the Essential Eight strategies.
Our endpoint and application management service shields your devices and applications from cyber threats. This includes regular application patching to minimise vulnerabilities.
Our services also cover managing application installation, securing Office Macros for authorised users, and strengthening applications and endpoints against cyber risks.
Our mobile device management (MDM) service empowers you to control applications, settings, and device tracking, with the ability to remotely reset devices in case of theft.
For custom security and efficiency solutions for your business, contact us at 1300 307 907.
Let Diamond IT drive your success.




