 It’s no secret that cyber-crime is on the rise, and that all organisations – not just large corporates and enterprises – need to take steps to secure their IT network.
It’s no secret that cyber-crime is on the rise, and that all organisations – not just large corporates and enterprises – need to take steps to secure their IT network.
But all the best security in the world will be for nothing if your organisation has a publicly facing Remote Desktop Server. What do I mean by publicly facing? In summary, if you can access your Remote Desktop Server from anywhere in the world by simply using the Remote Desktop Connection tool, your Remote Desktop Server is publicly facing (or ‘open’), which means you can access it conveniently, but so can cyber-criminals.
So you might be thinking at this point “but we’ve had a publicly facing Remote Desktop Server for many years, why is this a problem now”? This is a great question, and to explain, I’ll need to quickly explain some cyber-crime concepts.
The first thing you need to be aware of is a ‘botnet’. A botnet is an interconnected network of computers infected with malware without the user’s knowledge, which are controlled by cyber-criminals. Botnet’s can consist of hundreds of thousands of infected computers, all ready to perform any action the cyber-criminal controlling the botnet commands. Typically they’re used to send SPAM emails, which is one of the key ways cyber-criminals spread malware such as ransomware.
But in more recent years, these botnet’s are being tasked with the job of connecting remotely to open Remote Desktop Servers. Just being able to connect doesn’t of course mean they can login – they still need to correctly input a username/password combination. Which bring us to another important cyber-crime concept, ‘brute force attack’. A brute force attack is a trial and error method used to guess a username/password combination. In a brute force attack, automated systems (such as a botnet) are used to generate a large number of consecutive guesses as to the username/password combination.
Brute force attacks are nothing new. If you checked the logs of a Remote Desktop Server ten years ago, you’d see hundreds of brute force login attempts. Back then, the cyber-criminals were generally trying to login to Remote Desktop Servers using the administrator account, in the hope that the administrator account had a weak password.
But with the rapid increase in ransomware, cyber-criminals aren’t just trying to access your Remote Desktop Servers administrator account password, they’re satisfied with any account! That’s because ransomware can be effective using any account, even those with relatively low security privileges.
The following table shows the username’s used during a brute force attack of an open Remote Desktop Server in late 2016, showing attempts made in a 24 hour period:
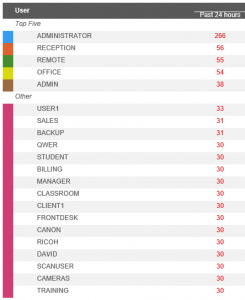
There are many more username’s that have been used in this brute force attack, with the above table showing only the most common. If any of these usernames have a weak password (such as ‘a’ or ‘password’), this network would be easily compromised. And what many don’t realise is that the attack might occur on an account that you’re not even aware of. In the above example, you’ll notice accounts such as ‘Ricoh’ or ‘Canon’ that can be setup by third party vendors to support a particular device.
What this all highlights is that organisations, no matter how large or small, need to be aware of the high risks of Remote Desktop Servers that are directly accessible via the Internet. There are many mitigation strategies that balance the need to be flexible, whilst maintaining a higher level of security. Most of these strategies are low cost, and easy for users to adopt and learn.
How can Diamond help?
If you have any concerns or questions surrounding your Remote Desktop Server, any aspect of your network’s security, or if we can assist in any way please fill out our online form below or call us today on 1300 307 907 or why not take our online security assessment below to gauge how vulnerable your business may be...
Diamond ICT Security Assessment
Take our tailored Security Assessment to gauge how protected your business is from potential online attacks...





