
“It’s organised crime,” states cyber security expert Jon Dimaggio, “it’s a modern-day version of the mob.” This is an opening statement on the recent episode of ABC’s Four Corners program, delving into who is responsible for Australia’s recent massive cyber security crimes.
Every seven minutes, a cyber attack is reported in Australia and businesses are paying tens of millions of dollars in ransom, the program claims. We wrote about some of the most breaches in history recently. Many more like this are anticipated.
These are not crimes committed by lone computer geeks wearing hoodies in a basement somewhere. In reality, global cyber crime is the third biggest economy in the world. Hacks like the Medibank and Optus incident are part of a sophisticated business operation. These cyber gangs operate just as an ordinary software company would, yet with highly illegal behaviour that threatens our personal data and even national security. Some of them even have HR departments and 'employee of the month' programs! Hackers take part in 'job interviews' to score a place in the syndicates.
In the Four Corners episode, Hackers Inc: Chasing the cyber crime syndicates attacking Australia, broadcast on 17 April, reporter John Lyons leads an investigation into who is responsible for one of Australia’s largest-ever data breaches. The Medibank hack threatened to expose a ‘naughty list’ revealing highly-sensitive health information of some of Medibank’s most influential customers. This was just the beginning of the hacking syndicates’ attempt to extort huge sums of money from the health insurance provider. The investigation takes the program as far as Ukraine where Russian cyber attacks are rife.
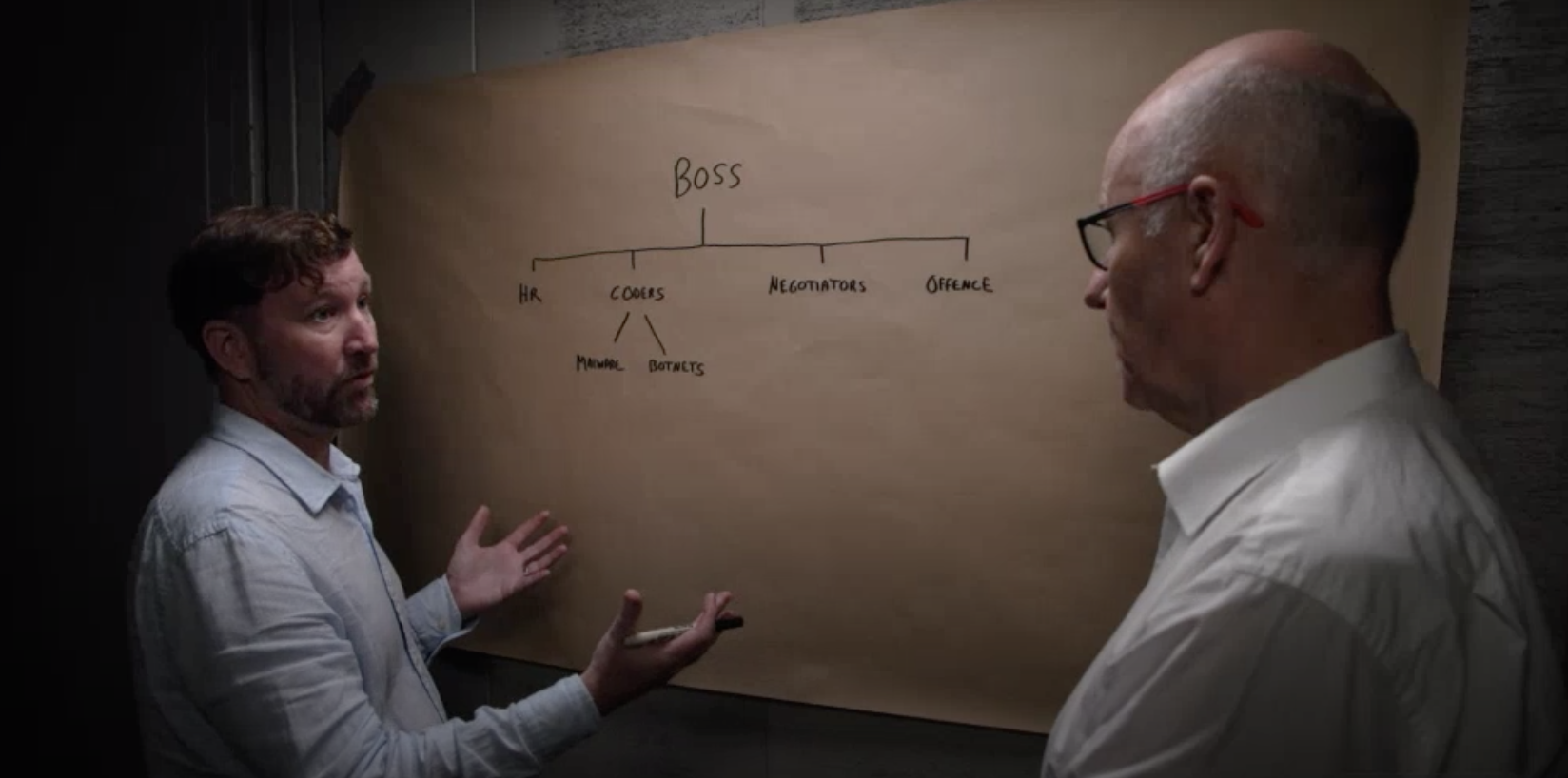
An expert explains how cyber criminal gangs work on the Four Corners Program.
The facts
- Cyber crime hurts many people and businesses. Stocks plummet, people lose their jobs, and widespread damage is caused.
- The Australian Government warns we must all brace for more attacks.
- Our cyber crime unit responds to hundreds of major incidents each year.
- The Government is considering making the payment of cyber crime ransoms illegal in an attempt to curb the crime.
“It is just a low act of a sub‑human type of person to take personal health information, the most private thing that you or I could have, and try to use that for money. It just disgusts me, and it does tell us that we are dealing with a particular type of scumbag here," - Clare O’Neil, Australia’s first Cyber Security Minister.
Who is behind these crimes?
It is believed that many of the hackers involved in the Medibank hack were based in Russia. However, the way the criminal groups operate makes tracking them difficult. Gangs sell access to software that harms a network, and they control ransom negotiations with the victims. However, it’s hackers, known as ‘affiliates’, that make the initial breach.
What is an affiliate?
These are people who buy into a ransomware or a cyber extortion model. Kind of like a franchise, wherein the ransomware, malware of the group’s Dark Web resources or portals for leaking information are rented.
As such, it can really difficult to determine exactly who is responsible for the crime.
According to expert testimony on the Four Corners program, there is founded suspicion that REvil were involved in the Medibank attack.
Who is REvil?
REvil (also known as Sodinokibi) is a sophisticated ransomware group that has been responsible for numerous high-profile attacks against organisations around the world. They are thought to be based in Russia.
REvil typically gains access to its victims' systems through phishing emails, exploit kits or by exploiting vulnerabilities in remote desktop protocols (RDP) or other software. Once inside a network, the group uses a variety of tools and techniques to map out the network, steal sensitive data and encrypt files. They then demand a ransom payment in exchange for a decryption key to unlock the files.
Affiliates are able to ‘rent’ the group’s malware to launch attacks.
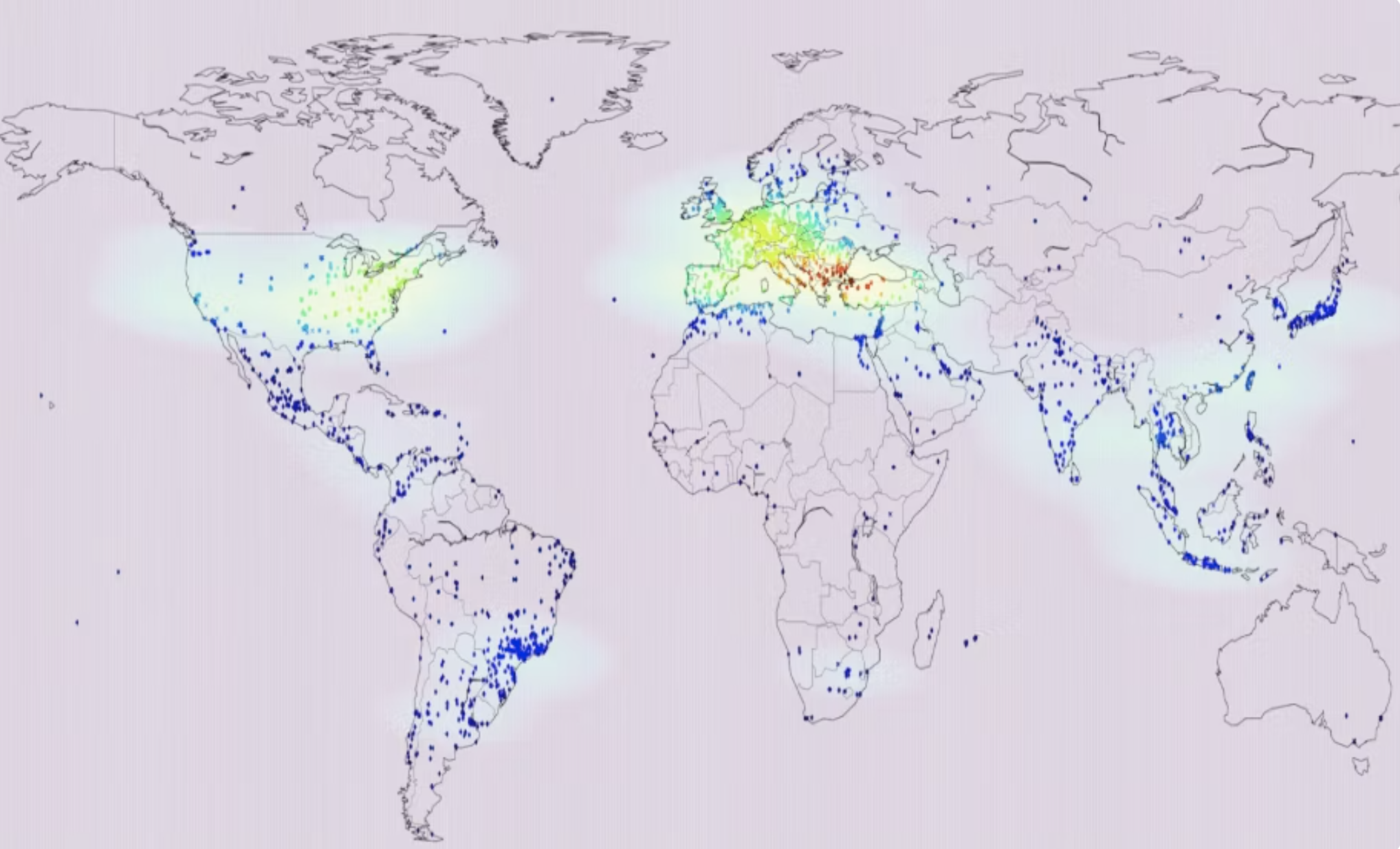 Based on visibility from McAfee's MVISION Insights, McAfee was able to generate an overview map of REvil ransomware infections observed from May through August 23rd, 2019:
Based on visibility from McAfee's MVISION Insights, McAfee was able to generate an overview map of REvil ransomware infections observed from May through August 23rd, 2019:
REvil is just one such cyber gang operating across the globe.
What's next?
Cyber crime is not going anywhere. In fact, the Government warns that more is to come.
Businesses must remain more vigiliant than ever. It is also worth considering your data collection practises. Do you need to keep all the data you hold? As a nation, are we too heavily storing data?
“Ultimately, what we see from these groups is they tend to be pretty good at out‑manoeuvring law enforcement. They will phoenix to avoid pressure, so when the heat is on from global law enforcement they will disband their group. They'll lie low for a bit, then they'll pop up again. Maybe they'll rebrand, for example, and we've seen that over and over again. So unfortunately it's going to be really hard for us to break the business model of cyber extortion”, says Katherine Mansted, Senior Fellow in the Practice of National Security at the ANU National Security College.
We strongly encourage you to read or watch the Four Corners episode: Hackers Inc: Chasing the cybercrime syndicates attacking Australia
>> Read the full transcript of the program here.
>> Watch the full Four Corners program here.
How Diamond IT can support you
Diamond IT will work with you to ensure your staff are aware of the types of ever-evolving cyber threats, and equip them with tools and a high level of cyber and data awareness and comprehension.
Our online Cyber Security Staff Awareness Training and Cyber Security Health Check can have an immediate impact on the strength of your security.
Our Business Technology Consultants are specialists in improving your internal cyber security. We offer a range of security solutions to ensure your employees and business remains secure, with many included in our Managed IT Services Agreements including:
- Multi-Factor Authentication
- Diamond Management Systems and Patching
- Cyber Security Awareness Training
- Cyber and Data Breach Consulting and Forensic Analysis
- Disaster Recovery (DR) Planning
- and more...
If you need advice on how you can ensure your cyber security strategy is fit for purpose, our team of cyber security experts are ready to help. Contact our team on 1300 307 907 today.





